Security Operations Center (SOC): Data Guardians
- Aastha Thakker
- Oct 28, 2025
- 6 min read

Every day, we hear the news of hacking, data breaches, attacks etc. Making cybersecurity a buzzword along with the constant pressure to secure our data and ourselves from different kind of threats. While, everyone is talking about hacking resources, let’s talk about securing them. Who secures these resources? We? If we, then do we go at every premise and secure their devices and data? That’s practically not possible, right?
What is SOC?
Here comes the role of SOC. Security Operation Centre (SOC) is a centralized unit, keeps a watchful eye on an organization’s entire computer system, 24/7, that deals with security issues on an organizational and technical level. This unit consists of different people who monitor, detect, analyze and respond to different threats or incidents.
SOC is like a security guard in front of your house, but way more advanced!

How do SOCs use SIEM and SOAR?
SIEM (Security Information & Event Management)
For security analysts, understanding SIEM is crucial. It is a tool that collects and analyses logs from all devices and systems across your organization.
Power of Logs: Every action on a device generates logs, essentially a record of activity. Think you IT system as your house. Every device, like a computer or phone, keeps a log of its activity, like a notebook recording who came and went. SIEM is like a central filing system for these notebooks. It collects everything, organizes it (fixing different formats and time zones), and puts it all in one place (aka ‘single pane of glass’). This makes it easier for security guards (analysts) to see everything that’s happening and spot any suspicious activity. Logs from different devices can have varying formats and timestamps due to time zone differences. SIEM normalizes these logs, ensuring consistency and enabling efficient analysis.
Detection: SIEM employs various techniques to identify suspicious activity from the massive amount of log data it collects. This includes:
Rule-based correlation: SIEM takes logs from various security sources and correlates them against pre-defined rules. These rules identify suspicious activity patterns, akin to establishing investigative criteria based on known threats.
User and Entity Behavior Analytics (UEBA): Next-generation SIEMs employ UEBA to establish baselines for user and entity behavior within the IT infrastructure. Deviations from established patterns can trigger alerts, mirroring the identification of anomalous activity by a security analyst.
Integrated case management and automation: Advanced SIEMs offer centralized case management capabilities. This allows for the consolidation of related alerts and streamlined investigations, fostering a collaborative environment for security teams. Additionally, these platforms can integrate with Security Orchestration, Automation, and Response (SOAR) tools, facilitating automated response actions to expedite threat mitigation.
SOAR (Security Orchestration, Automation, and Response)
It is designed to streamline an organization’s security posture. But what exactly is SOAR, and why is it becoming a cornerstone of modern cybersecurity strategies?
Three Pillars of SOAR
Security Orchestration: This involves bringing together various security tools and systems into a unified framework. SOAR acts as the conductor, ensuring all these tools work together seamlessly. It facilitates smooth communication and collaboration, allowing for a unified and efficient response to threats.
Automation: Repetitive tasks can bog down security teams, hindering their ability to focus on complex threats. SOAR automates these time-consuming activities, freeing up valuable time for analysts. This includes initial threat detection, incident triage, and response actions. Automation not only accelerates response times but also minimizes the risk of human error, allowing security teams to focus on more strategic initiatives.
Response: When an incident strikes, time is gold. SOAR platforms provide robust incident response capabilities. SOAR empowers security teams with pre-defined playbooks — standardized response protocols for specific threats. These playbooks automate critical actions:
* Threat intel gathering: Understand the attack’s nature and scope.
* Compromised system isolation: Minimize lateral movement and prevent further damage.
* Malicious IP blocking: Cut off attacker access and prevent intrusions.
* Stakeholder notification: Ensure everyone is informed for swift action.
What are playbooks for?
SOAR’s secret lies in its playbooks — automated blueprints for handling diverse security incidents. Let’s take an example of brute force attack. On a particular system, there is multiple failed login attempts, SOAR’s pre-defined brute-force playbook comes into action and acts according to the predefined instructions like:
Threat Assessment: Automated investigation to gather information about the attacker’s IP address, origin, and login attempts.
Adaptive Response: Based on the severity of the attack (e.g., number of attempts, source IP), the playbook can implement various measures:
a. Temporary Account Lockout: If the attempts originate from a single IP, the playbook can temporarily lock the associated account, hindering the attacker’s progress.
b. IP Blocking: In extreme cases, the playbook can blacklist malicious IP addresses, preventing further login attempts from that source.
c. Alert and Notification: The security team is automatically notified of the incident details, enabling them to take further action if needed.
While a brute force attack is a common example, SOAR playbooks can be customized to address a wide range of security threats. From phishing attempts to malware outbreaks,
Playbooks vs. Runbooks:Playbooks are strategic, offering a broad response overview. Runbooks are tactical, providing specific steps for individual tasks within the plan. Think of playbooks as the company’s emergency response plan, while runbooks are like detailed manuals for each scenario. Both are crucial for a well-coordinated response.
As cyber threats evolve, SOAR’s capabilities continue to grow. The integration of Artificial Intelligence (AI) and Machine Learning (ML) will further enhance SOAR’s ability to detect and respond to even the most novel threats. Additionally, cloud-based SOAR solutions are on the rise, offering greater flexibility and scalability for organizations of all sizes. SOAR empowers security teams to work smarter, not harder. By automating routine tasks, orchestrating workflows, and enabling swift incident response, SOAR grants security teams valuable time and peace of mind. Imagine a world where security analysts can focus on strategic threat hunting and proactive defense measures, leaving the repetitive tasks to SOAR.
How SIEM Works
1. Log Collection and Aggregation: SIEM starts by gathering log data from a wide range of sources across your network. This includes devices like firewalls, servers, applications, and even user activity. SIEM tools act like a vacuum cleaner, sucking up this data in real-time.
2. Log Parsing and Enrichment: Raw log data is messy and difficult to understand. SIEM takes this raw data and parses it into a structured format, making it easier to analyse. It can also enrich the logs with additional context, such as usernames, IP addresses, or device types.
3. Event Correlation and Security Analytics: This is where the magic happens. SIEM uses pre-defined rules and statistical analysis to examine the data for suspicious activity. Imagine a detective sifting through clues. SIEM looks for patterns, anomalies, and correlations between events from different sources. For example, it might identify failed login attempts happening at unusual times or unusual data transfer activity.
4. Threat Intelligence: SIEM can also leverage threat intelligence feeds. Think of this as giving your SIEM a cheat sheet of the latest hacking tactics. These feeds provide information about known threats and vulnerabilities, which SIEM can use to improve the accuracy of its analysis and prioritize potential security incidents.
5. Alerting and Incident Management: When SIEM identifies a potential threat, it generates an alert for the security team. The SIEM might also provide details about the event, such as the source, severity, and potential impact. Security analysts can then investigate the alert and take appropriate action, such as isolating compromised systems or blocking malicious traffic.
6. Reporting and Compliance: SIEM plays a crucial role in security reporting and compliance. It allows you to generate reports on security activity, track trends over time, and identify areas of risk. This information can be essential for demonstrating compliance with security regulations.
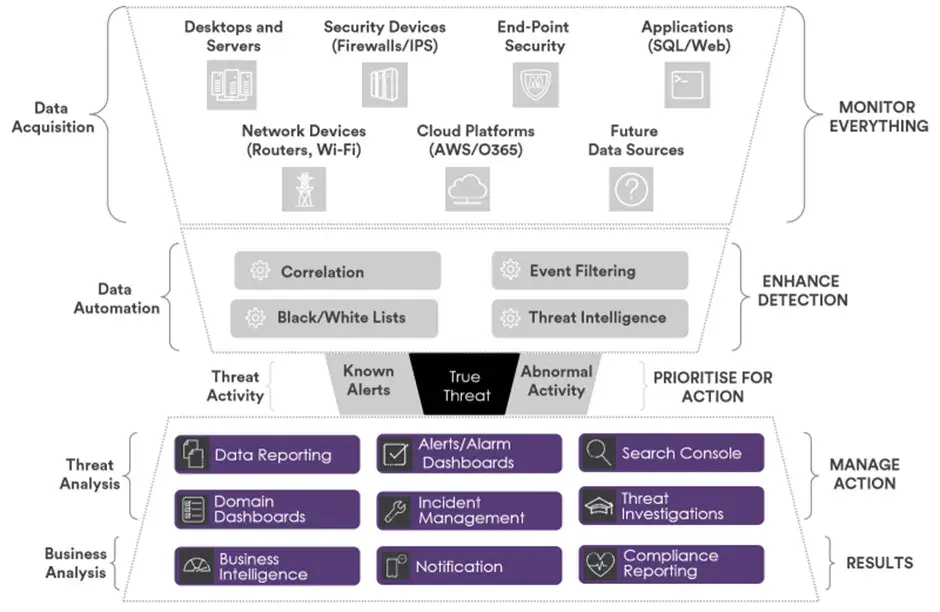
Components of SIEM

FAQs related to SOC
Q1: What are security logs?
Ans: The foundation of security monitoring. These are raw data records generated by devices and applications across your network, containing information about system activity. Examples include firewall logs, operating system logs, intrusion detection system (IDS) logs, application logs, and user activity logs.
Q2: What do you mean by Event Correlation?
Ans: The process of analzing security logs from various sources to identify potential threats. SIEM uses pre-defined rules and statistical models to find patterns, anomalies, and correlations between events that might indicate suspicious activity.
Q3: What exactly is ‘Security Event’?
Ans: A single occurrence within a security log that deviates from the expected norm. Security events can be triggered by failed login attempts, unusual file access, malware detection, or other suspicious activities.
Q4: What do you understand by ‘False Positive’?
Ans: A security event that triggers incorrectly, signifying a potential threat that turns out to be harmless.
Q5: What do you mean by Security Incident?
Ans: A confirmed or suspected security event that poses a potential risk to your organization’s assets, such as data breaches, unauthorized access attempts, or malware infections. When a security event meets specific criteria defined in your Security Incident and Event Management (SIEM) policy, it escalates to a security incident.
Q6: What is ‘Incident Response (IR)’?
Ans: A structured process for detecting, analysing, containing, eradicating, and recovering from a security incident. The IR process involves various activities like threat identification, containment actions, evidence collection, incident documentation, and post-incident review.
Q7: What is ‘Threat Intelligence’?
Ans: Information about current and emerging security threats, vulnerabilities, and attacker tactics, techniques, and procedures (TTPs). SOC analysts leverage threat intelligence feeds to improve the accuracy of SIEM correlation rules.
These are the fundamentals of SOC you need to know before diving in! Have any questions about SOC or specific topics you’d like to know more about?
DM or comment below for the same.
See you next Thursday with more exciting content!



Comments