HR Honeypot: Hackers Flip the Script on Job Market Scams
- Aastha Thakker
- Oct 29, 2025
- 4 min read

Cybersecurity has become more than just a buzzword — it’s a critical aspect of business operations. While many associate cybersecurity with protecting social media accounts or personal data, professionals in the field know it’s far more complex. As the demand for cybersecurity experts grows, so does the number of job seekers in this field. Finding a job in this field can be tough, with many fake or unpaid internships out there. But that doesn’t stop eager candidates from sending out resumes.
Hackers Posing as Job Applicants
cybercriminals have noticed this flood of job applications and saw an opportunity. They’re now targeting the hiring process itself. By pretending to be job seekers, these attackers are trying to trick HR teams and sneak into companies. It’s a clever move that turns the job hunt into a potential security risk for businesses.
Imagine you’re an HR professional, sifting through resumes to find the perfect candidate for an open position. It’s a routine task, right? But what if that seemingly innocent resume was actually a Trojan horse, designed to infiltrate your company’s network? This is exactly the kind of threat we’re facing, and it’s more sophisticated than ever.
A well-established hacker group, typically known for attacking big international banks and financial companies, has changed its tactics. Instead of going after money directly, they’re now pretending to be job applicants to trick HR professionals and recruiters.
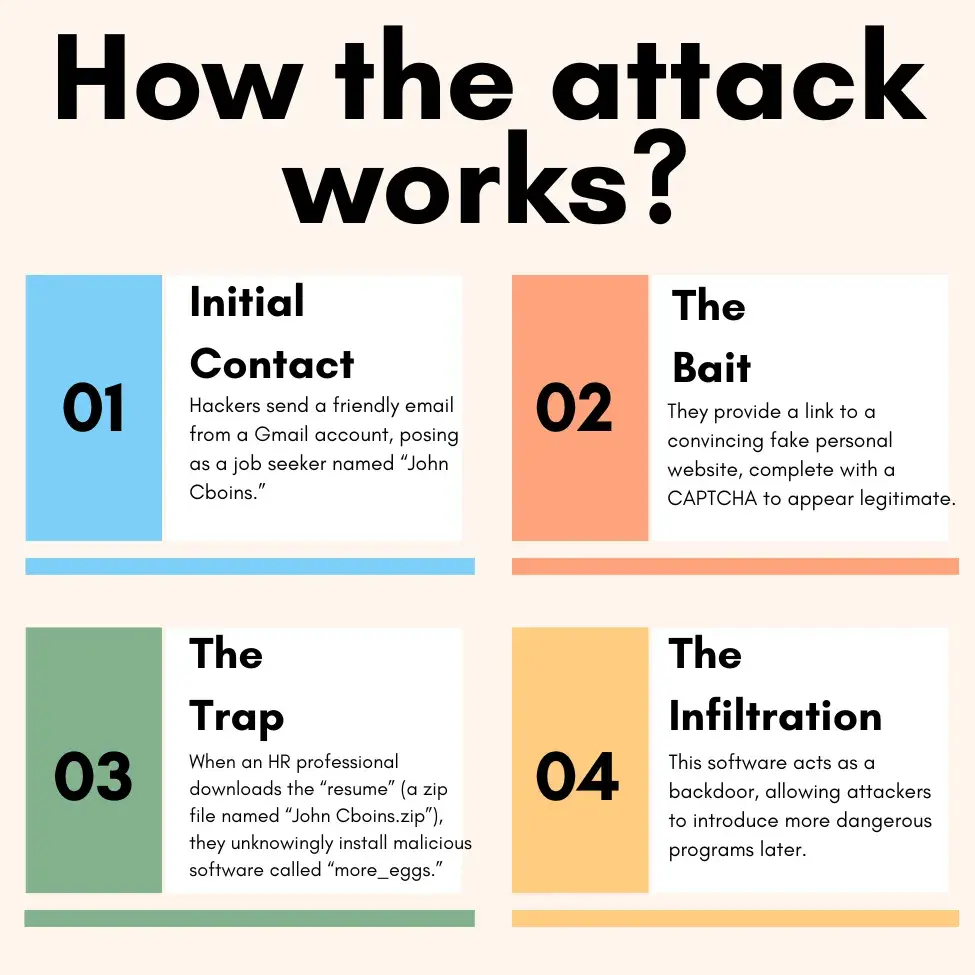
How the attack works?
Cybersecurity experts at a company called Trend Micro found out about this trick. They discovered that the hackers are using a tool kit called “Golden Chickens”, which is like a ready-made hacking package that criminals can buy and use. The specific program they’re using is written in a language called JScript.
The experts think a group known as FIN6 might be behind this, as they’ve used similar methods before. But it’s hard to be 100% sure because many different hacker groups use these “hacking toolkits”, making it tricky to pinpoint exactly who’s responsible.
This new approach shows how cybercriminals are getting creative, turning the job application process into a way to break into companies’ computer systems. It’s a reminder that in the digital world, even something as ordinary as reviewing resumes can become a security risk if we’re not careful.
Hackers sent it from a Gmail account pretending to be someone named “John Cboins”. This email went to a high-ranking person at the company they were targeting. Interestingly, the email didn’t have any suspicious links or attachments. Instead, it was just a friendly message, trying to build trust with the receiver.
After this first contact, someone in the HR department downloaded what they thought was a resume. It was a zip file named “John Cboins.zip”. The researchers aren’t sure exactly where the HR person got the link to download this file, but they used Google Chrome to get it.
When the experts looked closer at where this file came from, they found a very convincing fake website. This website looked just like a normal job seeker’s personal site. It even had one of those annoying “prove you’re not a robot” tests (called a CAPTCHA). This made the whole thing seem very real and trustworthy.
The hackers put a lot of effort into making everything look normal and safe. This clever setup could easily fool a busy recruiter into thinking they were just talking to a regular person looking for a job, not a dangerous hacker.
The “more_eggs” Malware
“More_eggs” is part of a hacking toolkit called Golden Chickens, sold by a group known as Venom Spider. This malware has been around since at least 2017 and has targeted various organizations, from banks to mining companies.
Delivery Methods:
Fake job documents with hidden scripts
LinkedIn and email phishing with job offers
ZIP files disguised as images
Fake resume websites
Protecting Your Organization

Alright, we’ve covered those sneaky email job scams. But hold on, ’cause there’s another digital troublemaker (another email trickster).
The Zimbra Email Server Vulnerability
What is Zimbra?
Zimbra is an email and collaboration software platform. Think of it as a professional-grade email system, similar to Microsoft Outlook or Gmail, but with some key differences:
It’s typically used by businesses and organizations rather than individuals.
It can be installed on a company’s own servers, giving them more control over their data.
Besides email, it includes features like calendars, contact lists, and file sharing.
It’s open-source, which means organizations can customize it to fit their needs.
The Vulnerability
A serious security flaw (CVE-2024–45519) has been found in Zimbra email servers.
Attackers can run harmful code on these servers by just sending specially crafted emails.
How It Works
The flaw is in Zimbra’s “postjournal” service, which handles incoming emails.
Attackers put malicious commands in the “CC” field of an email.
When the server processes the email, it accidentally runs these commands.
Current Situation
Hackers are actively exploiting this vulnerability.
The attacks started soon after researchers shared details about the flaw.
Attack Method
Attackers send emails that look like they’re from Gmail.
These emails have fake addresses and harmful code in the “CC” field.
If successful, the attack installs a “webshell” on the server.
This webshell lets attackers control the server remotely.
Discovery and Confirmation
First reported by Ivan Kwiatkowski from HarfangLab.
Confirmed by experts at Proofpoint.
Solutions and Recommendations
Update Zimbra to the latest secure version:
Version 9.0.0 Patch 41 or later
Versions 10.0.9 and 10.1.1
Zimbra 8.8.15 Patch 46 or later
If possible, turn off the “postjournal” service.
Check and fix the “mynetworks” settings to block unauthorized access.
Urgency
Server administrators should act quickly to apply updates or protective measures.
The vulnerability is being actively exploited, making prompt action crucial.
It’s crucial for organizations to stay vigilant and adapt their security measures. By understanding these new threats and implementing robust cybersecurity practices, businesses can protect themselves from these sophisticated attacks targeting the hiring process and email systems.
In the world of cybersecurity, staying informed and proactive is your best defense against emerging threats.
To all the HRs out there — thank me later, of course. We truly respect the art of recruiting new talent into the company (yes, it’s an art!). So how about this… let’s make a deal — never reject my application, okay? 😉



Comments