top of page
Search


Sleep Mode Isn’t Safe: How Attackers Exploit Systems
The Myth: “Sleep Mode = Safe Mode” You close your laptop lid, hear that satisfying click, and walk away thinking your data is secure. After all, the screen’s locked, right? Wrong. That convenient “sleep mode” millions rely on daily isn’t the security blanket we think it is. While your device appears dormant, it’s actually maintaining a treasure of sensitive information in active memory; encryption keys, passwords, cached credentials, and open documents all sitting vulnerable
Aastha Thakker
5 min read

From Man-in-the-Middle to Browser-in-the-Middle
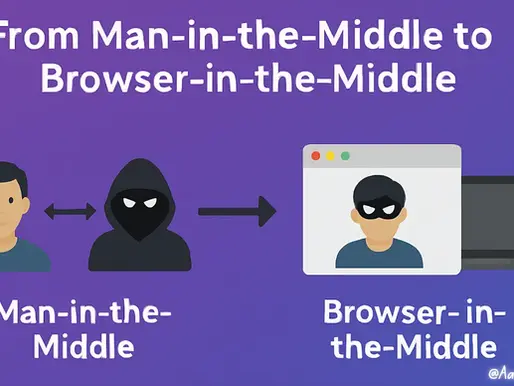
What is a Man-in-the-Middle Attack? A Man-in-the-Middle (MITM) attack is a cyberattack where a malicious actor secretly positions themselves between two communicating parties at the network level. MITM Attack Process MITM attacks typically unfold through a systematic three-phase approach: 1. Interception Phase: Attacker establishes themselves as an intermediary in the communication channel using various techniques: ARP Spoofing : Manipulating network address tables to redire
Aastha Thakker
3 min read


Know the Toxic Duo or They’ll Know you: ToxicPanda and WinOS 4.0 Malware
🎉 Celebrating 1 Year of My Blogging Journey! 🎉 Exactly one year ago today, on the early morning of November 2, 2023, I took a leap of faith and hit “publish” on my first blog post. It was a moment filled with hesitation, self-doubt, and a million questions: “Will it be good enough? Will people even read it?” But sometimes, all you need is a little push from the people around you. To everyone who believed in me, motivated me, and helped spread my words, thank you from the bo
Aastha Thakker
7 min read
bottom of page