IoT Access Technologies: Powering the Connected World
- Aastha Thakker
- Oct 29, 2025
- 7 min read

Welcome back to our continuing exploration of IoT! In our previous sessions, we’ve covered the fundamentals of IoT, including its core concepts, digitization, and various architectures. We’ve also seen the basics of sensors and actuators, which form the backbone of IoT systems.
Today, we’re shifting our focus to IoT access technologies. These are the critical communication methods and protocols that enable IoT devices to connect, interact, and share data effectively. In this part we will be learning IEEE 802.15.4, IEEE 802.11ah, and LoRaWAN, along with a brief look at 6LoWPAN.
IEEE 802.15.4
The naming convention for IEEE 802.15.4 follows a specific pattern used by the Institute of Electrical and Electronics Engineers (IEEE) for their standards. Let’s break it down:
IEEE: This is the organization that develops and maintains the standard.
802: This number represents the family of standards for local and metropolitan area networks.
15: Within the 802 family, 15 specifically refers to Wireless Personal Area Networks (WPANs).
4: This is the specific standard number within the WPAN group.
So, IEEE 802.15.4 is the fourth standard developed by IEEE for Wireless Personal Area Networks. It defines the physical layer and media access control for low-rate wireless personal area networks (LR-WPANs).
This standard is particularly important for IoT because it forms the basis for several popular IoT protocols, including ZigBee, Thread, and Wireless HART.
IEEE 802.15.4 is a wireless access technology for low-cost and low-data-rate devices that are powered or run on batteries. This access technology enables easy installation using a compact protocol stack while remaining both simple and flexible.
You’ll often find IEEE 802.15.4 technology powering smart home and building systems, Industrial wireless sensor networks, automotive networks, and even interactive toys and remote controls.
Physical Layer
The IEEE 802.15.4 standard supports multiple physical layer (PHY) options for different frequencies in the Industrial, Scientific, and Medical (ISM) bands.

Later versions introduced additional PHY options, including:
OQPSK PHY: Uses offset quadrature phase-shift keying for reliable data transmission
BPSK PHY: Employs binary phase-shift keying for simpler data encoding.
ASK PHY: Utilizes amplitude shift keying and BPSK modulation for improved range and throughput
MAC Layer
The Media Access Control (MAC) layer in IEEE 802.15.4 manages channel access and coordinates data frame routing. Key functions include:
Network beaconing
PAN association and disassociation
Device security
Reliable link communications
The MAC layer uses four frame types:
Data frame: Handles all transfers of data
Beacon frame: Used in the transmission of beacons from a PAN coordinator
Acknowledgement frame: Confirms the successful reception of a frame
MAC command frame: Responsible for control communication between devices
Network Topology
IEEE 802.15.4 networks can be structured in three main ways:
Star topology
Peer-to-peer topology
Mesh topology — better coverage and reliability.
In an IEEE 802.15.4 network, every Personal Area Network (PAN) must have a unique PAN ID, which all nodes in that network must use. For example, if a network has a PAN ID of 1, all nodes in that network should be configured to use this ID. An FFD can communicate with any other device in the network, whereas an RFD can only communicate with FFDs
These networks consist of Full-Function Devices (FFDs) and Reduced-Function Devices (RFDs), with at least one FFD serving as the PAN (Personal Area Network) coordinator which helps other devices join the network and facilitates communication.
In mesh networks, the IEEE 802.15.4 standard doesn’t specify how to choose communication paths (called path selection) within the MAC layer. This can be managed at using standard routing protocols like the IPv6 Routing Protocol for Low Power and Lossy Networks (RPL).

Security
IEEE 802.15.4 employs the Advanced Encryption Standard (AES) with a 128-bit key for data security. It not only encrypts data but also validates it using a Message Integrity Code (MIC).
To enable AES encryption in IEEE 802.15.4, the frame format is slightly altered, and part of the payload is used for security features. This is done by setting the Security Enabled field in the Frame Control section of the 802.15.4 header to 1. This single-bit field indicates that security features, including AES encryption, are enabled for the frame
IEEE 802.11ah: Wi-Fi for IoT
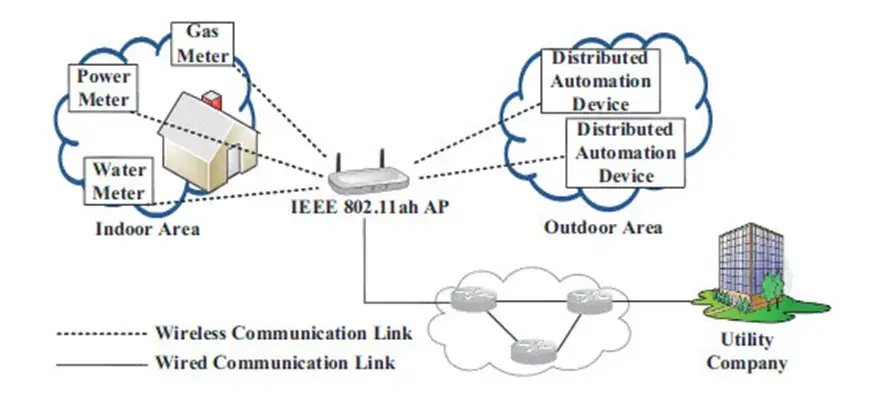
IEEE 802.11ah, also known as Wi-Fi HaLow, is a version of Wi-Fi tailored for IoT applications. It operates in sub-GHz frequency bands, offering extended range and lower power consumption compared to traditional Wi-Fi. It connects high-data-rate devices like fog computing nodes, sensors, and audio or video analytics devices. It also supports Wi-Fi backhaul infrastructures in various environments like smart cities and industrial areas.
IEEE 802.11ah is designed for three main use cases:
Sensors and Meters in Smart Grids: Used for environmental monitoring, industrial sensors, healthcare systems, and home automation.
Backhaul Aggregation: Connecting industrial sensors and meter data, and potentially integrating IEEE 802.15.4g subnetworks.
Extended Range Wi-Fi: Providing long-range Wi-Fi for outdoor hotspots or offloading cellular traffic where standard Wi-Fi isn’t sufficient.
Physical Layer
IEEE 802.11ah uses Orthogonal Frequency-Division Multiplexing (OFDM) modulation with channel widths of 1, 2, 4, 8, or 16 MHz. These channels are narrower than those used in IEEE 802.11ac, which operates at 5 GHz with channel widths up to 160 MHz. As a result, 802.11ah channels offer about one-tenth the data rates of 802.11ac. The sub-GHz frequency bands (not licensed) used vary by region:
868–868.6 MHz: Europe, Middle East, Africa, Russia
902–928 MHz: North America, Asia-Pacific
314–316 MHz, 430–434 MHz, 470–510 MHz, 779–787 MHz: China
MAC Layer Enhancements
IEEE 802.11ah introduces several MAC layer improvements to support IoT applications:
Increased device support (up to 8192 devices per access point)
Efficient communication Shortened MAC header allows more efficient data transmission
Null Data Packet (NDP) Extends to control and management frames, making communication more efficient and saving power by avoiding unnecessary decoding of the MAC header and data payload.
Grouping and sectorization: Uses sector antennas and groups stations to reduce network contention, improving performance in large networks.
Restricted Access Window (RAW) to control network access to avoid simultaneous transmissions, reducing collisions and saving power.
Target Wake Time (TWT) Allows devices to wake up only at scheduled times, conserving energy and reducing network collisions.
Speed Frame Exchange: Enables efficient frame exchange during reserved times, reducing medium contention and extending battery life by keeping devices in low-power states when not in use Network Topology
Topology
IEEE 802.11ah uses a star network topology with a central access point. It includes a relay function to extend range. This means one device can act as a relay to pass data to another device further away, similar to a mesh network. The clients, not the AP, manage this relay function. Usually, it involves two hops. Devices closer to the AP use higher transmission rates, while those further away use lower rates. This keeps the system efficient and ensures that close devices don’t experience slow communication.
Sectorization helps manage interference and reduce collisions in areas with many clients. It divides the coverage area into sectors using an antenna array and beam-forming techniques. This way, each sector has less interference, making communication smoother and more reliable, especially in large coverage areas with multiple access points.
LoRaWAN: Long Range, Low Power
LoRaWAN is a Low-Power Wide-Area (LPWA) technology designed for long-range, battery-powered devices. It’s particularly well-established & supported by a substantial industry alliance for IoT solutions requiring extended coverage.
Physical Layer

LoRaWAN Frequencies:
LoRaWAN uses unlicensed sub-GHz bands, mainly in the 400–900 MHz range.
Different regions use slightly different frequencies. For example:
Europe: 863–870 MHz
North America: 902–928 MHz
Australia: 915–928 MHz
LoRa Gateways:
Think of a LoRa gateway as a smart radio tower in the center of a star-shaped network.
It can listen to many devices at once, even if they’re talking over each other.
Gateways act like translators, passing messages between your devices and the internet.
Adaptive Data Rate (ADR):
ADR is like an automatic tuner for each device in the network.
It adjusts how loud and how fast each device talks to find the perfect balance.
This helps save battery life and makes sure everyone in the network gets heard.
Remember, LoRa is all about long-range, low-power communication. It sacrifices speed for distance and efficiency, making it perfect for IoT devices that need to send small amounts of data over long distances while preserving battery life.
MAC Layer
LoRaWAN Device Classes:
Class A (All devices):
Most energy-efficient
Sends data, then briefly listens for responses
Two short receive windows after each transmission
Ideal for battery-powered sensors
2. Class B (Beacon):
More frequent receiving opportunities
Uses gateway beacons for synchronization
Scheduled receive windows
Balances power and responsiveness
Note: Was experimental in LoRaWAN 1.0.1
3. Class C (Continuous):
Always listening when not transmitting
Lowest latency for downlink communication
Highest power consumption
Suitable for mains-powered devices
Key points to remember:
All LoRaWAN devices must support Class A
Classes are designed to optimize battery life vs. communication needs
Progression from A to C increases receive availability but also power use
Choice of class depends on application requirements and power constraints
Network Topology
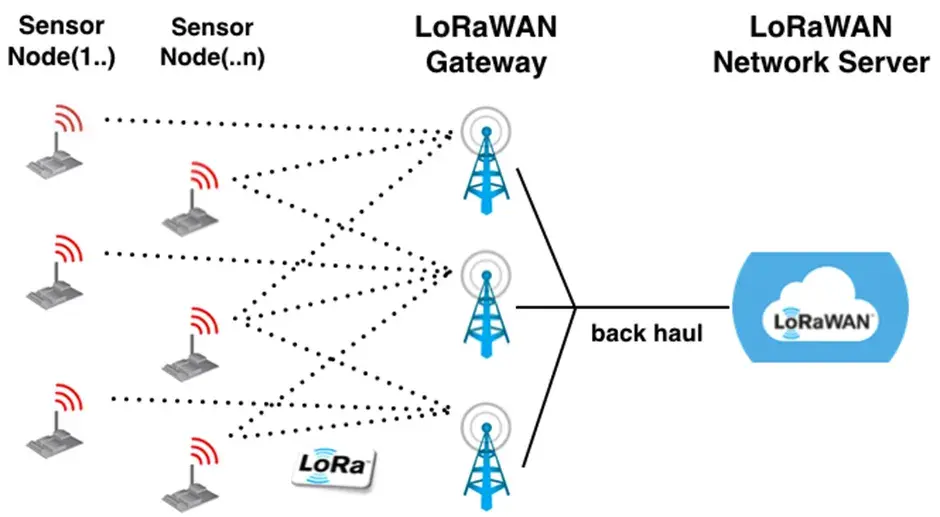
LoRaWAN Network Topology: “Star of Stars”
Structure:
Endpoints -> Gateways -> Network Server -> Application Servers
2. Key Components:
Endpoints: Sensors/devices (battery-powered)
Gateways: Bridge between endpoints and network (IP-connected)
Network Server: Central management and optimization
Application Servers: Process and utilize data
3. Communication:
Endpoints to Gateways: LoRa radio (long-range, low-power)
Gateways to Network Server: Standard IP
4. Unique Features:
Multi-gateway reception: Improves reliability
Packet de-duplication: Network server function
Adaptive Data Rate (ADR): Optimizes performance and battery life
5. Data Handling:
MAC Layer: LoRaWAN protocol
PHY Layer: LoRa modulation
Upper Layers: Flexible (e.g., ZigBee, CoAP, MQTT)
6. Network Server Role:
Traffic management
Device configuration
Network optimization
Security
Network Security (MAC Layer): Ensures endpoint authentication and protects LoRaWAN packets using AES encryption.
NwkSKey: A network session key shared between endpoints and the LoRaWAN network server, used to ensure data integrity (via MIC checks) and to encrypt/decrypt MAC-level messages.
AppSKey: An application session key used between the endpoint and the application server to encrypt/decrypt data and ensure application-level integrity.
AppKey: A unique AES-128 key provided by the application owner, derived from a root key controlled by the provider.
Gateway Security: LoRaWAN gateways should be secured using VPN or IPsec to protect traffic and network operations.
6LoWPAN: Bridging IPv6 and Low-Power Networks
6LoWPAN (IPv6 over Low-Power Wireless Personal Area Networks) is a protocol that enables the transmission of IPv6 packets over IEEE 802.15.4 networks. It’s crucial for integrating small, low-power devices into the broader Internet of Things ecosystem.
Key features of 6LoWPAN include:
IPv6 compatibility
Low-power operation
Efficient packet delivery through header compression
Mesh networking support
Interoperability with larger IP networks
6LoWPAN networks consist of:
6LoWPAN nodes (sensors, actuators)
Edge routers (gateways to larger IP networks)
Mesh routers (intermediate routing nodes)
6LoWPAN: Advantages and Challenges
Advantages:
Robust Mesh Networking:
Self-healing and scalable
Flexible routing (one-to-many, many-to-one)
Energy Efficiency:
Sleep mode for leaf nodes
Extended battery life
Cost-Effective:
Low-cost communication for large-scale IoT
IPv6 Integration:
Direct cloud routing
Seamless integration with IP networks
Scalability:
Supports numerous devices
Ideal for smart cities and industrial IoT
Flexibility:
Wide range of IoT applications
IPv6-based compatibility
Basic Security:
Suitable for many IoT scenarios
Can be enhanced with additional measures
Challenges:
Security in Resource-Constrained Environments:
Balancing encryption with low power usage
Network Management:
Complexity in large-scale deployments
Need for efficient monitoring tools
Wireless Reliability:
Susceptible to interference
Requires robust error correction techniques
Comparison of IoT Access Technologies
To help you better understand the differences and similarities between these technologies, here’s a comparison table summarizing their key features:

See you next Thursday, till then digest this knowledge.



Comments